Dangerous games. How Trojans that attack gaming platforms work Developers of modern multiplayer games create entire virtual universes endowed not only with their own mythology and
Dangerous games. How do Trojans attack gaming platforms

The developers of modern multiplayer games create entire virtual universes, endowed not only with their own mythology and physical laws, but also with their own economic system. In the game worlds, there are always artifacts and ammunition that give the player certain advantages or allow you to change the appearance of the character. Ammunition can be obtained in battle, found, obtained by solving a certain task or completing a quest, or you can simply buy it. This is exactly how some gamers earn their living: they sell game items accumulated by overwork, or even entire accounts with a pumped character.
And where there is a smell of profit, all sorts of gray schemes inevitably emerge. For example, back in 2011, The Guardian correspondents wrote about prisoners in Chinese prisons who were forced by guards to engage in farming – to get loot and game currency, which was then sold for real money. Soon virusmakers also joined the division of the pie, and began distributing Trojans under the guise of cheats and trainers to steal from users of game accounts. And in 2014, the spread of malware was recorded that stole not Steam accounts, but individual game items, and in an extremely ingenious way.
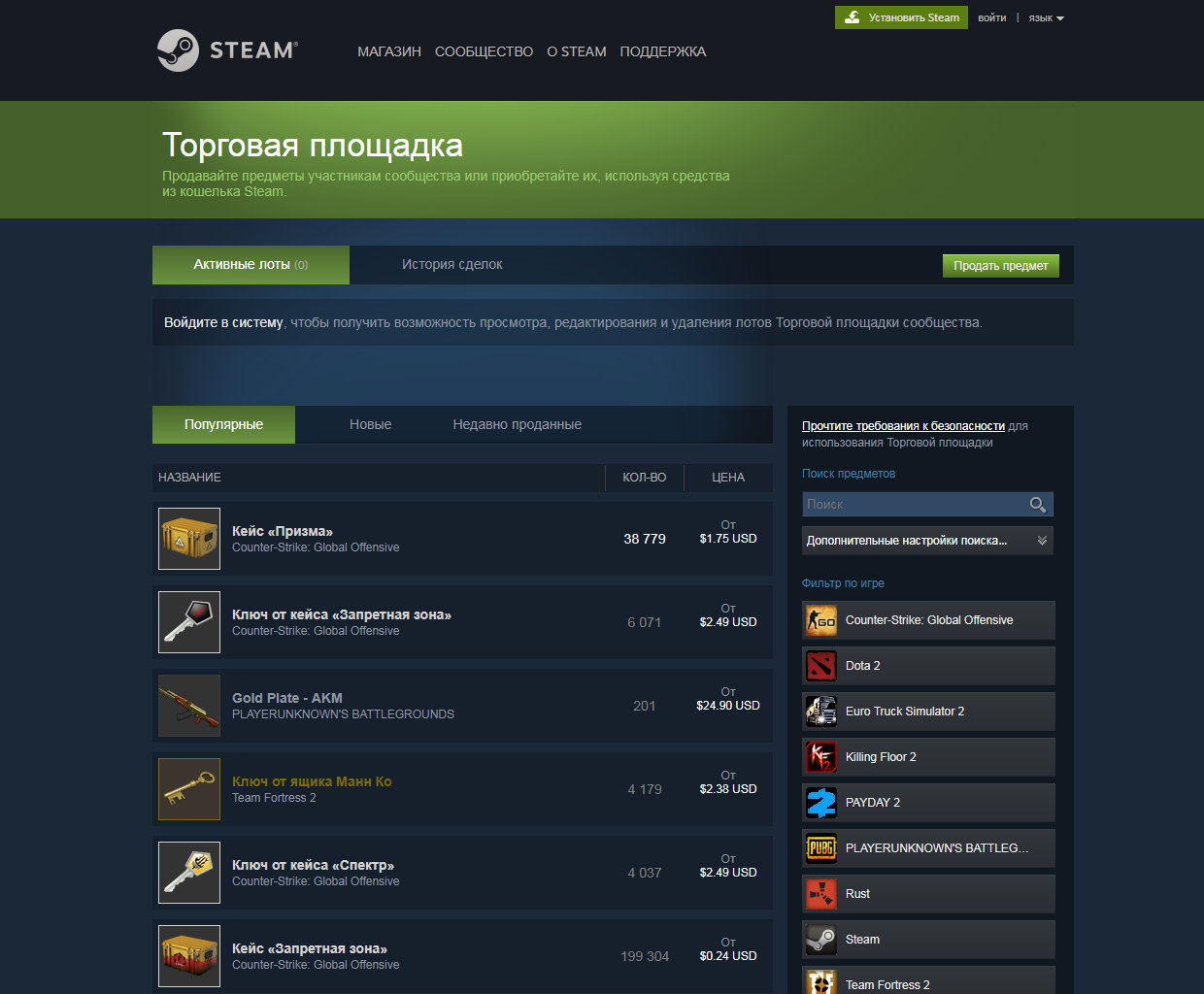
This is what a typical in-game item store looks like on Steam
Steam Burglar
In the summer of 2014, CS:GO users began to mysteriously lose their game inventory, about which they wrote alarmed messages on Reddit. Immediately before the incident itself, the player received a message in the Steam chat from another user with an offer to exchange virtual items. The message contained a screenshot of the inventory offered for exchange, while the deal itself looked quite profitable. After the successful completion of the operation, the user logged into the game and was surprised to find that part of his most valuable property had disappeared in an unknown direction.
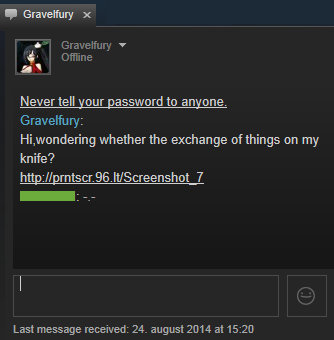
Such messages were received by affected users
Thanks to the investigation conducted by analysts, it was possible to establish the root cause of the tragedy. It turned out to be the SteamBurglar Trojan. While the unsuspecting user was looking at an expensive item in the chat window that was offered to him for exchange for some mediocre trinket, the troy found the Steam process in the computer’s memory and pulled out information about the ammunition in the user’s arsenal. Then, this list was searched using the keywords rare, mythical, immortal, legendary, arcana and key (the list of keywords can be configured in the troy's admin panel) – thus SteamBurglar chose the most valuable inventory.The trunks found, the Trojan immediately put up for sale through Steam at a very favorable price. The proceeds came to the expense of the viramaker.
Trojan himself and builders himself were successfully offered to him at cheat forums, and Troy allowed to steal objects not only from CS: GO, but also from other toys: Dota 2, Team Fortress 2, Warframe.
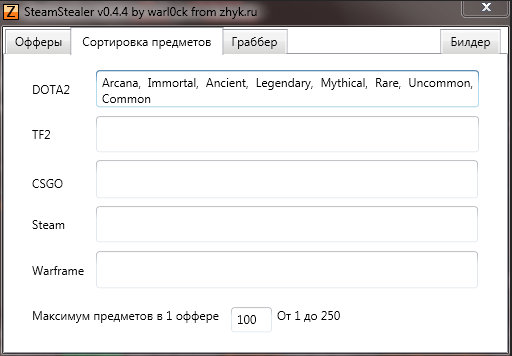
This is how Steamburglar brusher looked like a builder
To send messages, Steamburglar users used third-party tools, but in December 2014 the author rolled out the update of Troy, which allowed to spam in chats directly from the Adminki application. In response to the outraged messages of the Steam, the Steam administration was at first freezing, offering to independently search for users on the pages of the market of the villains and complain about them in support. However, under the pressure of the public, they nevertheless changed the procedure for selling game items, after which mandatory confirmation by e-mail was required to make such transactions.
Continuation is available only to participants
Option 1. Join the XAKEP.RU community to read all materials on the site
During the specified period, membership in the community will open access to all the Hacker materials, allow you to download issues in PDF, turn off advertising on the site and increase a personal funded discount! Read more




